Security is one of the biggest factors working against WordPress right now, but it doesn’t have to be. It’s easy to achieve a secure WordPress install if you start off on the right foot. Luckily for you, I have three simple instructions to get you rolling in the right direction:
Achieve a Secure WordPress Install by Installing in a Directory.
It’s no secret the URL for the WordPress Dashboard is wp-admin. Unfortunately, just about every malicious user has this knowledge. One way to get an upper hand and add a easy layer of security is to install WordPress in a directory. By installing WordPress in a directory, you are adding an extra section into the Dashboard login URL. Consider the following:
A typical WordPress scenario would have the following login URL:
http://www.awesomesite.com/wp-admin/
When WordPress is installed into a directory, the Dashboard might have the following URL (depending on your directory name):
http://www.awesomesite.com/gds32s/wp-admin/
In this example, WordPress is installed out of gds32s. When adding this simple snippet to the URL of your Dashboard, you’ve instantly raised your defenses from bots who automatically go around the internet sniffing for login screens by simply adding wp-admin to the end of every URL they discover.
Read more about giving WordPress its own Directory in the WordPress Codex.
Achieve a Secure WordPress Install by Enabling Limited Login.
Even with your extra layer of security in a directory install, an advanced bot might still discover your WordPress Dashboard URL, but it doesn’t have to be the end of the world. Once the WordPress Dashboard URL is discovered, there is no doubt the bot will begin to Brute Force Attack your login window. A Brute Force Attack is essentially when a computer just starts randomly guessing your username and password until it gets it right. The first rule of thumb here is to obviously have a relatively secure password, but you can also add an additional layer of security by frustrating the bot/hacker using a Limited Login Window as we detailed in a post earlier.
Achieve a Secure WordPress Install by Changing the Database Prefix.
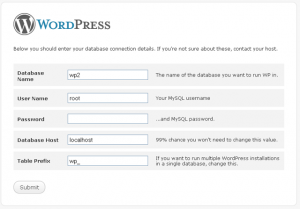
One thing unique about WordPress is it’s open source. The way it works is in no way a secret to anyone. Open source software always has endless benefits to the end user; however, in terms of malicious use, having an open source can occasionally have its downfalls. In this instance, the downfall is when installing WordPress it suggests you use a Table Prefix of wp_ as shown below:
While the logic behind this makes sense, it doesn’t make sense for a secure wordpress install, as it gives the hacker a head start in what he’s looking for. This is easily fixable by simply clicking where it says Table Prefix and changing wp to just about anything else you can think of. As long as it has no spaces and ends with a _ WordPress should allow it without complaint.
By following these three simple steps you may not have guaranteed yourself a bullet proof WordPress site (actually, not bullet proof at all,) but it does give you an upper hand by providing a few false leads for a low-level hacker.